前言
最近比赛的题目,复现一下。
正文
unctf
web题目环境没有了,暂时无法复现(网站进不去了,等可以进去了再复现)
Crypto
鞍山大法官开庭之缺的营养这一块怎么补
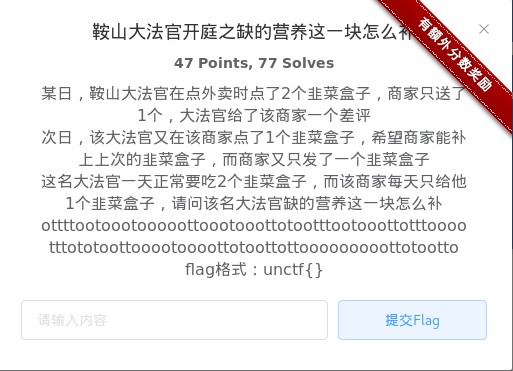
ottttootoootooooottoootooottotootttootooottotttooootttototoottooootoooottotoottottooooooooottotootto培根密码,why?因为ot只有这两种字母,而且在说吃的。
放到在线网站解密
PEIGENHENYOUYINGYANG
所以flag是unctf{PEIGENHENYOUYINGYANG}
easy_rsa
已知a,b,e,c然后还知道a=p+q, b=p-q脚本跑
import gmpy2 as gp
from Crypto.Util.number import *
c = 22886015855857570934458119207589468036427819233100165358753348672429768179802313173980683835839060302192974676103009829680448391991795003347995943925826913190907148491842575401236879172753322166199945839038316446615621136778270903537132526524507377773094660056144412196579940619996180527179824934152320202452981537526759225006396924528945160807152512753988038894126566572241510883486584129614281936540861801302684550521904620303946721322791533756703992307396221043157633995229923356308284045440648542300161500649145193884889980827640680145641832152753769606803521928095124230843021310132841509181297101645567863161780
q = 155422298738009940394189206134042119662513162560610248399569107132538620220590060772127789136918984458521940817304671619205395736161534795149599241668486283754795346411784845057685713557075371605135986388011998610261360520650827734187124699589734496097678970899686056997267797534053934064148348759788335157899
p = 164976388739628973581511063883090363893890874421691770454048880284500992179926996908823840726558454111596699286948761026319434957217223527703429627592448959262532954019810985574583860227624287638908448719207441426500367172146028171043107126122608800640249201232870138119493156975216320985668013888561826953269
n = p * q
phi = (q - 1) * (p - 1)
e = 65537
d = gp.invert(e, phi)
m = pow(c, d, n)
print(long2str(m))flag为UNCTF{welcome_to_rsa}
简单的RSA
只有一个txt文件,里面是e,n,c的值,e的值特别大,从大师傅那里收来的脚本。跑一下出结果
import gmpy2
from Crypto.PublicKey import RSA
import CTF.RSA.ContinuedFractions as ContinuedFractions
import CTF.RSA.Arithmetic as Arithmetic
from Crypto.Util.number import long_to_bytes
def wiener_hack(e, n):
# firstly git clone https://github.com/pablocelayes/rsa-wiener-attack.git !
frac = ContinuedFractions.rational_to_contfrac(e, n)
convergents = ContinuedFractions.convergents_from_contfrac(frac)
for (k, d) in convergents:
if k != 0 and (e * d - 1) % k == 0:
phi = (e * d - 1) // k
s = n - phi + 1
discr = s * s - 4 * n
if (discr >= 0):
t = Arithmetic.is_perfect_square(discr)
if t != -1 and (s + t) % 2 == 0:
print("Hacked!")
return d
return False
def main():
e = 18437613570247445737704630776150775735509244525633303532921813122997549954741828855898842356900537746647414676272022397989161180996467240795661928117273837666615415153571959258847829528131519423486261757569454011940318849589730152031528323576997801788206457548531802663834418381061551227544937412734776581781
n = 147282573611984580384965727976839351356009465616053475428039851794553880833177877211323318130843267847303264730088424552657129314295117614222630326581943132950689147833674506592824134135054877394753008169629583742916853056999371985307138775298080986801742942833212727949277517691311315098722536282119888605701
c = 140896698267670480175739817539898638657099087197096836734243016824204113452987617610944986742919793506024892638851339015015706164412994514598564989374037762836439262224649359411190187875207060663509777017529293145434535056275850555331099130633232844054767057175076598741233988533181035871238444008366306956934
d = wiener_hack(e, n)
m = pow(c, d, n)
print(long_to_bytes(m))
if __name__ == "__main__":
main()Misc
baba_is_you
在010editor中打开附件,末尾处发现一个b站的URL,打开在评论区看到了flag
爷的历险记
这个有两个解,一个可能是预期解,还有一个不是预期解的。
先说预期解,就是玩游戏,先开宝箱,将base64编码解出,输入密码得到百度大法这个魔法攻击,然后就开宝箱,不过最多只能买到两个hint,第一个hint是爷经常在自己书房的花盆下做奇奇怪怪的事
另一个hint是爷看了自己的存档,rpgsave到底是什么呢
最后的hint就是flag,但是没钱买,搜索rpgsave找到在线修改的网站,
在线网站
将文件传入,修改gold,最后就可以买flag了。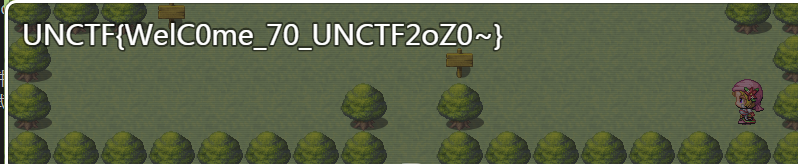
非预期解,在www/data/Items.json中搜索unctf
找到flag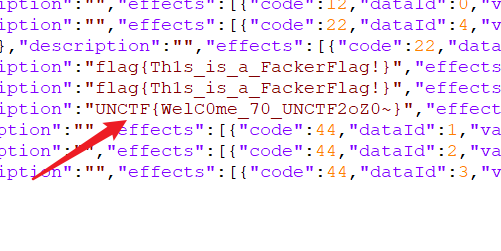
撕坏的二维码
打开文件得到一张残缺的二维码,右上角的定位符缺少一个,所以补上一个定位符就可以扫描出来结果了。
被删除的flag
这个就是拖到010editor中搜索unctf直接出flag
阴阳人编码
下载后得到txt文件,里面都是就这.、不会吧!、就这¿
它与Ook编码的格式很像,所以改成和Ook编码格式相同的类型。
在记事本中替换,就这.换成.不会吧!换成!就这¿换成¿
最后进行网站在线解码得到flag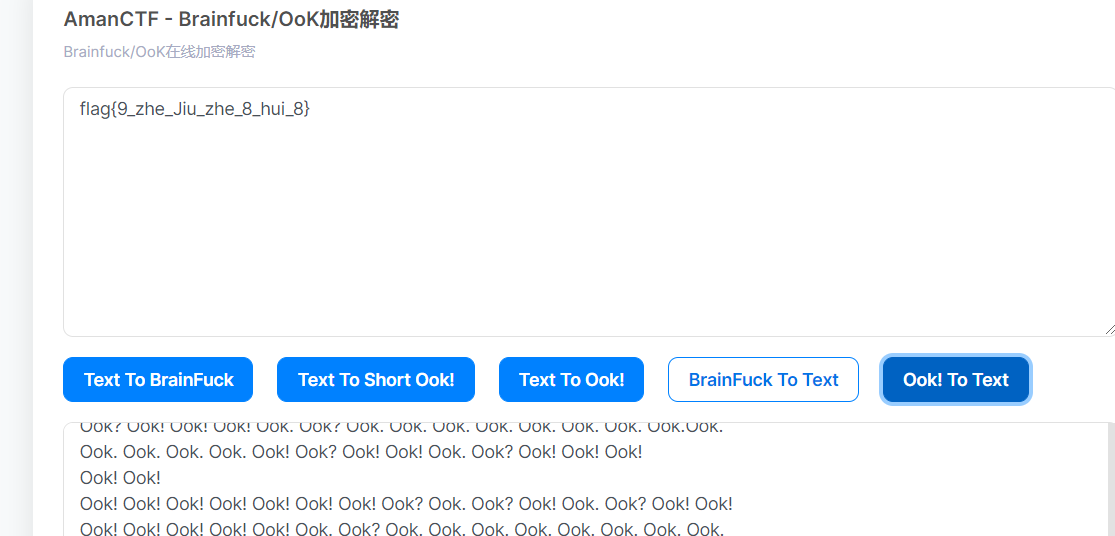
倒影
exe文件无法运行,用010editor打开,看文件头,发现是张图片的格式,往下翻,在最后发现了base64编码。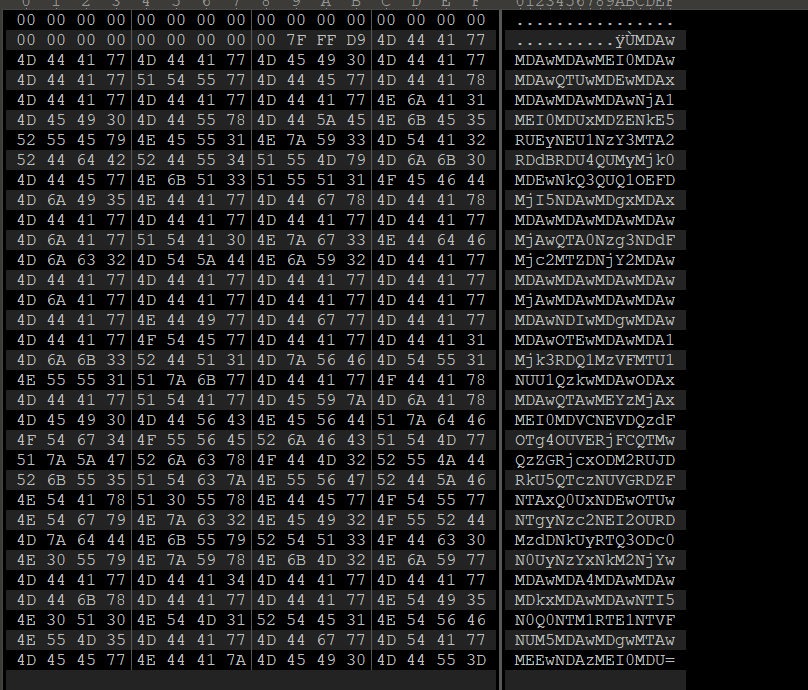
复制出来,解码得到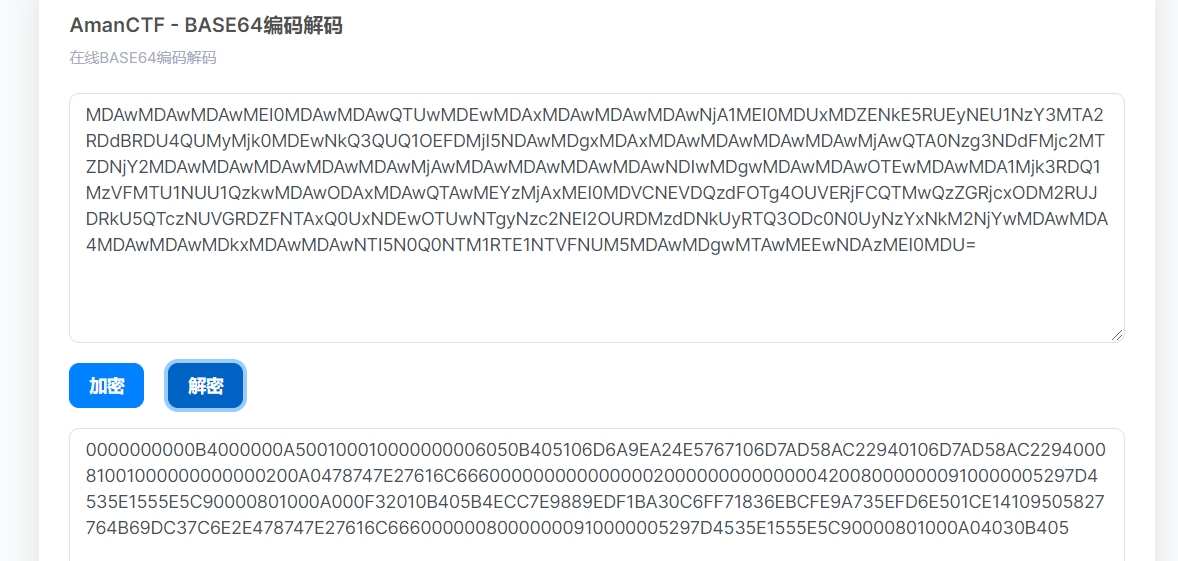
看最后,B405,是504B反过来了,所以先将它进行转换,反着输出
python代码
str = '0000000000B4000000A500100010000000006050B405106D6A9EA24E5767106D7AD58AC22940106D7AD58AC229400081001000000000000200A0478747E27616C666000000000000000200000000000000420080000000910000005297D4535E1555E5C90000801000A000F32010B405B4ECC7E9889EDF1BA30C6FF71836EBCFE9A735EFD6E501CE14109505827764B69DC37C6E2E478747E27616C66600000080000000910000005297D4535E1555E5C90000801000A04030B405'
print(str[::-1])得到结果
504B03040A00010800009C5E5551E5354D79250000001900000008000000666C61672E747874E2E6C73CD96B46772850590141EC105E6DFE537A9EFCBE63817FF6C03AB1FDE9889E7CCE4B504B01023F000A00010800009C5E5551E5354D792500000019000000080024000000000000002000000000000000666C61672E7478740A002000000000000100180004922CA85DA7D60104922CA85DA7D6017675E42AE9A6D601504B050600000000010001005A0000004B0000000000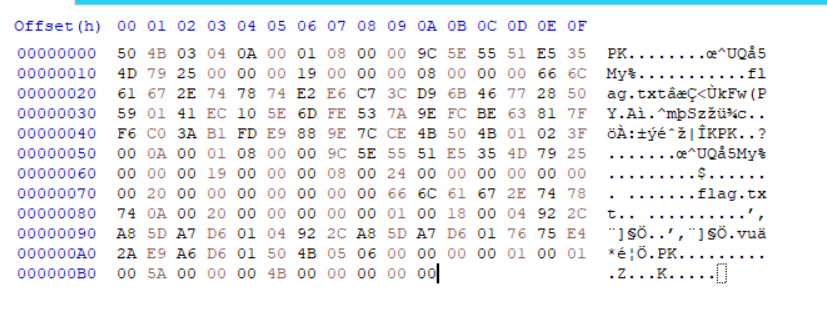
解压需要密码,没有任何提示这里的密码,所以尝试爆破。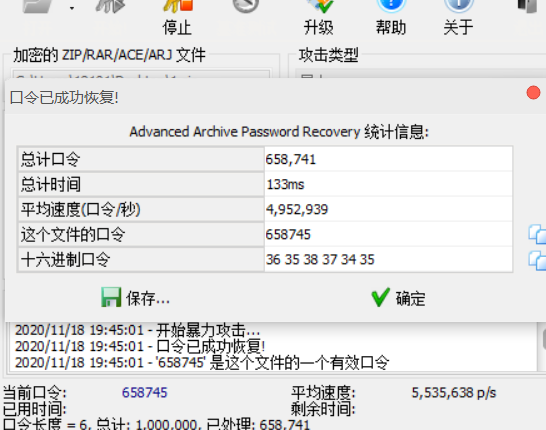
密码658745得到flag
你能破解我的密码吗
这个就是个破解shadow文件的内容的,首先想到的是使用John破解就可以了。
一条命令
john --show shadow用户名是guguguguji的,这个是有密码的。
guguguguji:$1$AH$xtjky.3kppbU27tR0SDJT.:18556:0:99999:7:::可以直接在线网站搜索查询。cmd5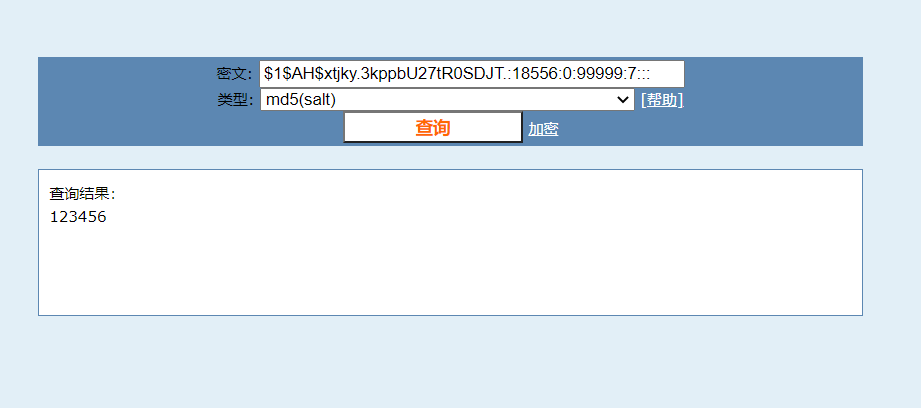
然后进行MD5加密就是flag
mouse_click
下载得到流量包,分析一下,全是USB流量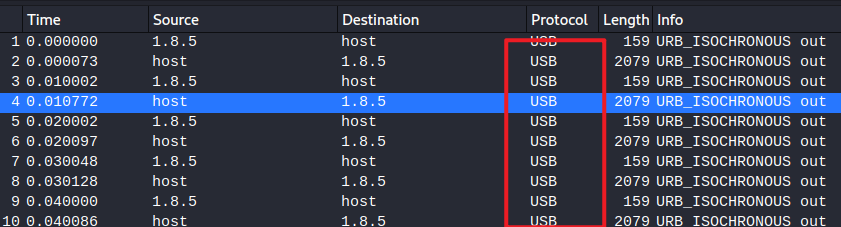
鼠标流量分析,之前总结过,直接套路解
tshark -r mouse_click.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt提取出来没有长度不一的,所以就不用进行二次处理了。
加冒号,转坐标。
之后直接画图就可以了。
最后得到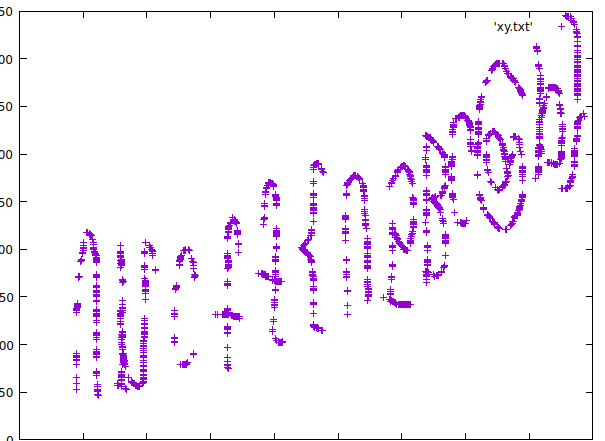
看的不方便,垂直反转一下。unctf{U5BC@P}
EZ_IMAGE
一共225个图片,225开方得到15,所以是15x15
montage拼图,
montage *.jpg -tile 15x15 -geometry +0+0 1.jpg得到
再使用gaps还原,具体安装方法之前总结过,直接百度即可找到。
gaps --image=1.jpg --population=500 --size=60 --save
网络深处
附件下载后得到
题目内故事纯属虚构,完全架空。
你是一名学生,你在夜间路过一个电话亭,一个人鬼鬼祟祟的进入电话亭拨通了一个电话又拿出手机录了音,他反常的行为引起了你的注意,他走后你决定去电话亭看看。
电话亭里又一个皱巴巴的纸条,上面写着一串数字:636806841748368750477720528895492611039728818913495104112781919263174040060359776171712496606031373211949881779178924464798852002228370294736546700438210687486178492208471812570216381077341015321904079977773352308159585335376746026882907466893864815887274158732965185737372992697108862362061582646638841733361046086053127284900532658885220569350253383469047741742686730128763680253048883638446528421760929131783980278391556912893405214464624884824555647881352300550360161429758833657243131238478311219915449171358359616665570429230738621272988581871,这很可能是刚才的人不小心丢在这里的,这显然不是电话号码,这使你更加好奇,你决定看看他拨的是什么电话号码。
你按了一下重拨键,想看看他拨打的电话号码,但是这个公用电话的屏幕坏了,之传出了一段拨号音,你迅速挂掉电话又重拨了一次并录下了拨号音。
回到寝室的你像弄清楚字条的含义,看来只有得到他拨打的电话才能搞明白字条的含义了。
得到电话号码以后,你拨通了他,里面传出一段杂音,一筹莫展的你决定将这件奇怪的事情告诉警察。
# 电话号码就是压缩包密码使用dtmf2num.exe提取按键音。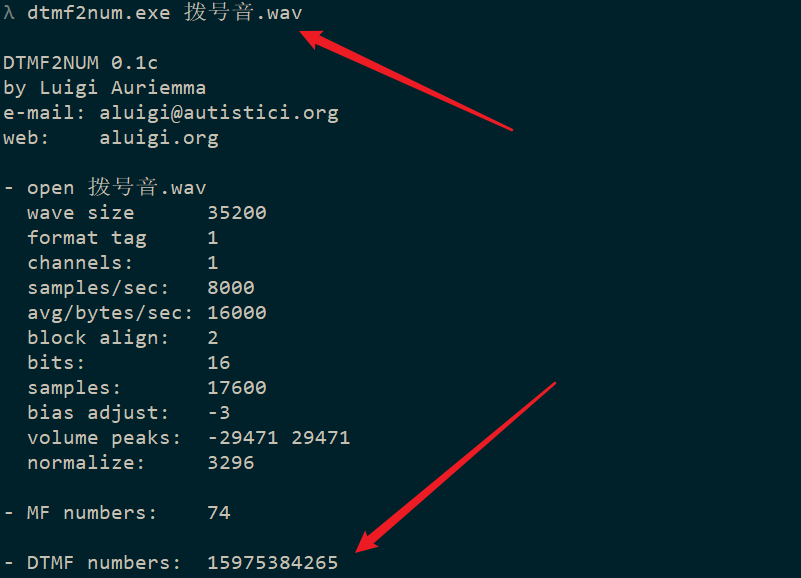
得到密码
解开压缩包
你是一名警察,前段时间有一个学生上报了一个可疑事件,一个人鬼鬼祟祟的打了一通电话又录了音,离开时不小心落下一个意义不明的字条。这名学生给了你一段拨号音,拨号音得到的电话号码,以及那个奇怪的字条。你拨通了那段电话并录了音,里面传出一段刺耳的奇怪录音,录音中可能就有关于字条破解方式的提示,你决定找到字条的秘密。
破解了字条以后,得到一个似曾相识的字符串。
# 得到的字符串就是flag,flag格式为flag{}
你认得这字符串,是某种处理过的字符串,解码以后出现了一个熟悉的单词,看来有必要查查这个人了。
# 不能再往下出了,有缘再见吧还有一个音频,拖进 audacity
打开频谱图,得到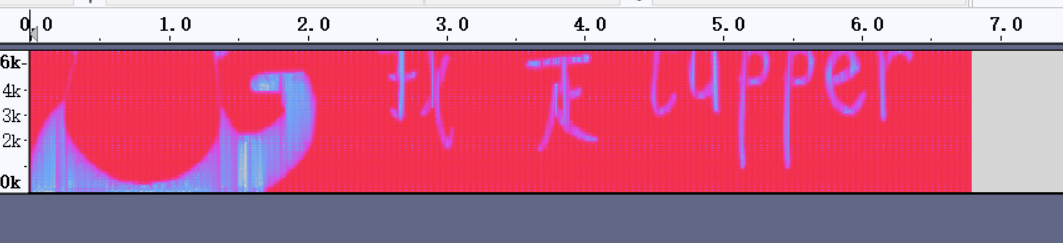
我的和别人的有点不一样,,别人的可以直接看到是tupper
可以搜索一下关键字,根据大师傅的wp找到一篇文章
用Tupper自我指涉公式造图
k就是第一段描述中的那一串神秘字符串。
"""
Copyright (c) 2012, 2013 The PyPedia Project, http://www.pypedia.com
<br>All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
# Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
# Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND
ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES;
LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND
ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT
(INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS
SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
http://www.opensource.org/licenses/BSD-2-Clause
"""
__pypdoc__ = """
Method: Tupper_self_referential_formula
Link: http://www.pypedia.com/index.php/Tupper_self_referential_formula
Retrieve date: Tue, 11 Mar 2014 03:15:49 +0200
Plots the [http://en.wikipedia.org/wiki/Tupper's_self-referential_formula Tupper's_self-referential_formula]:
: <math>{1\over 2} < \left\lfloor \mathrm{mod}\left(\left\lfloor {y \over 17} \right\rfloor 2^{-17 \lfloor x \rfloor - \mathrm{mod}(\lfloor y\rfloor, 17)},2\right)\right\rfloor</math>
The plot is the very same formula that generates the plot.
[[Category:Validated]]
[[Category:Algorithms]]
[[Category:Math]]
[[Category:Inequalities]]
"""
def Tupper_self_referential_formula():
k = 636806841748368750477720528895492611039728818913495104112781919263174040060359776171712496606031373211949881779178924464798852002228370294736546700438210687486178492208471812570216381077341015321904079977773352308159585335376746026882907466893864815887274158732965185737372992697108862362061582646638841733361046086053127284900532658885220569350253383469047741742686730128763680253048883638446528421760929131783980278391556912893405214464624884824555647881352300550360161429758833657243131238478311219915449171358359616665570429230738621272988581871
#love yiran
def f(x,y):
d = ((-17 * x) - (y % 17))
e = reduce(lambda x,y: x*y, [2 for x in range(-d)]) if d else 1
f = ((y / 17) / e)
g = f % 2
return 0.5 < g
for y in range(k+16, k-1, -1):
line = ""
for x in range(0, 107):
if f(x,y):
line += "@"
else:
line += " "
print line
#Method name =Tupper_self_referential_formula()
if __name__ == '__main__':
# print __pypdoc__
returned = Tupper_self_referential_formula()
if returned:
print str(returned)找到脚本,画图
g和9傻傻分不清楚,试一下就好了。
- 本文链接:https://m0re.top/posts/c75f537d/
- 版权声明:本博客所有文章除特别声明外,均默认采用 许可协议。

您可以点击下方按钮切换对应评论系统,
Valineutterances